- LastPass can now monitor employees' rogue reliance on shadow SaaS - including AI tools
- HPE 'morphs' private cloud portfolio with improved virtualization, storage and data protection
- Believe it or not, Microsoft just announced a Linux distribution service - here's why
- How to Stay Compliant with the New HIPAA Security Rule Updates
- AI agents bring big risks and rewards for daring early adopters, says Forrester
Private 5G Network Security Expectations Part 2

Privacy & Risks
The importance of proof of “security” concepts in private 5G networks:
Are verifications of system operations and new functions sufficient for your proof of concept in private wireless networks?
July 05, 2022
Read time: ( words)
The implementation of private 5G is already real, according to a survey conducted by Trend Micro in collaboration with 451 Research, part of S&P Global Market Intelligence in four countries (Germany, the U.K, Spain, the U.S.) across the manufacturing, electricity, oil and gas, and healthcare industries. Eighteen percent of respondents are already deploying private wireless 5G networks at production sites, and 6% are in the PoC (Proof of Concept) stage. Including those under consideration, more than 60% of the respondents are using or considering private 5G.
As I mentioned in a previous blog, the survey has found that improving security is the most important aspect when considering private wireless networks. This time, we will unravel the user’s awareness of implementing security measures in private 5G use cases that were revealed in the survey.
Security Concerns in Private Wireless Network
The introduction of the private wireless network will create new value for the enterprise and at the same time add new attack surfaces from a cybersecurity perspective.
The survey shows that exposure of data carried on the network (31%) and compromise of the network equipment (28%) on the network are the top security concerns in private wireless networks.
As if to respond to these concerns, the most critical security aspects were the data transiting the network (25%) and devices in the network core (20%), while other answers were dispersed. The introduction of new technologies may be a sign that sufficient security assessments have not yet been carried out. (Figure 1)
Figure1
Q: What is the most critical aspect of a private wireless network to secure?
Base: n = 408 Source: 451 Research custom study
Private Wireless Network Risk Evaluation
The first step in a security assessment begins with a risk evaluation on the target system. In the survey, only 8% of the respondents said they would do their own risk evaluation for the most important private 5G use cases in their environment. More than one third (37%) are expected to do this jointly with their partners, and 21% rely entirely on their partners for risk evaluation. (Figure 2)
Of course, partners and third parties can provide an objective view of potential risks, and their expertise can provide depth of risk identification and control. On the other hand, the extremely low rate of completing risk assessments on their own may be a sign of lack of confidence in risk analysis in a private 5G environment.
Security assessments, also known as information security assessments, are the process of determining how effectively an entity being assessed (for example: a host, system, network, procedure, or person—known as the assessment object) meets specific security objectives. (NIST SP800 115)
From this perspective, we need proof of “security” concepts that reflect the security goals of corporate security when private wireless networks deploy in enterprises.
Figure 2
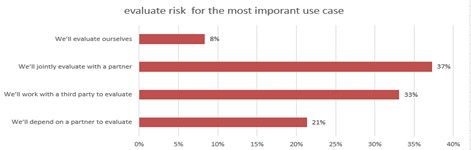
Q: For your most important use case, how will you evaluate risk?
Base: n = 408 Source: 451 Research custom study
Respondents seem to feel that the risks posed by the introduction of private wireless are caused by vulnerabilities. Four of the top five of the most important attack vectors are related to vulnerabilities. (Figure 3)
Figure 3
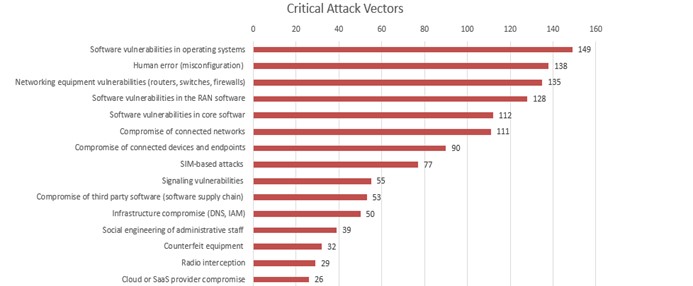
Q: What type of technology partner is most attractive to you?
Base: n = 408 Source: 451 Research custom study
Unfortunately, these concerns are well founded.
In 2021, underground threat actors teamed up as RaaS (ransomware as a service) group with a weaponized combination of malware, exploits, and tools to plague organizations in healthcare, insurance, manufacturing, transportation, and oil and gas industries around the world.
Our field tests on the security of private 5G also point out the possibility of intrusions due to these vulnerabilities.
In the survey, about 80% of respondents said they intend to connect their existing enterprise network or ICS network with Private Wireless Network in some way.
Figure 4
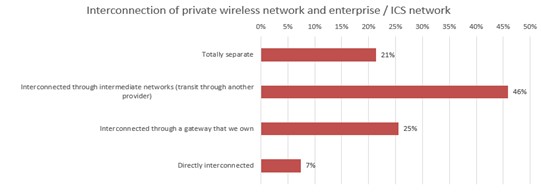
Q: To what extent will or does the private wireless network connect to your enterprise network or ICS network?
Base: n = 408 Source: 451 Research custom study
In this case, the risk assessment and security consideration of the private wireless network should be advanced not only for the private network alone, but also for the network security of the entire company connected to them.
Enterprises are promoting the use of private wireless networks, but when introducing these new technologies, we suggest that not only is confirmation of functional requirements such as 5G performance and system operation crucial at PoC stage, but also promoting proof of enterprise “security” concepts.
To read the executive summary of this survey, visit: https://resources.trendmicro.com/IoT-5G-Networks-Report.html
Methodology
This report was commissioned by Trend Micro and leverages data from a survey conducted in the U.S., Germany, U.K. and Spain. The survey consisted of about 400 respondents from the mentioned countries with job titles of director and above, across the manufacturing, power supply, oil and gas, and healthcare industries.
Sample titles of respondents include:
– VP/director of IT operations/CIO
– Director of IT, network operations/network architect/datacenter infrastructure and planning, network planning, 5G strategy planning, network virtualization, edge computing/MEC strategy and other equivalent roles.
We queried decision-makers who are aware of their company’s private 5G wireless networking strategy and implementation plans, deployment plans and security concerns.
Trend Micro provides industry-specific security solutions that include IT, OT, and CT (Communication Technology) represented by Private 5G.
https://www.trendmicro.com/en_us/business/solutions/iot/ics-ot.html
Trend Micro 5G Security for Enterprises
https://www.trendmicro.com/en_us/business/solutions/iot/enterprise-5g-iot.html
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

